Workflow of Third-party Authentication in Catalyst Applications
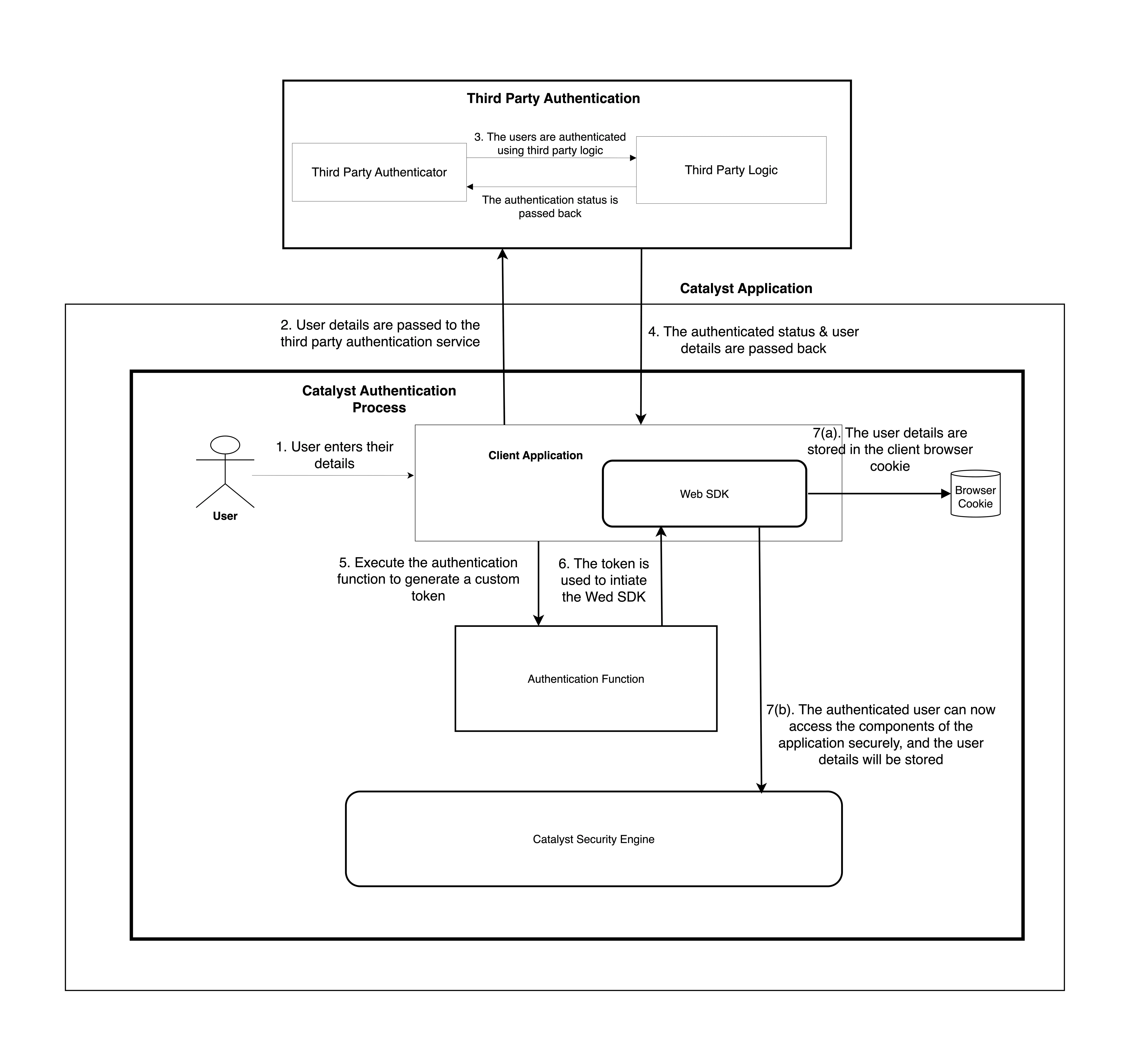
The following is a step-by-step drill down of the process of how an end-user authenticated by a third-party authentication service will log in to your Catalyst application:
-
When the end-user enters their details to log in to your application, they will be forwarded to the third-party authentication service that you have chosen.
-
The user details will be verified and stored in the database of the third-party service after the authentication logic is passed.
-
The user details will then be passed to the Catalyst client application.
-
The details will then be redirected to the authentication function that you code. This authentication function must include the Catalyst server-side script to generate a custom server token for the authenticated user.
-
This token will then be passed to the Web SDK incorporated in the client code.
-
The user will be logged in to your application using a JSON Web Token (JWT) generated from the client script, which will contain the authenticated user’s details.
-
(a). The user will now have access to the components of your application through its endpoints. Catalyst Security Engine ensures that all Catalyst components associated with the application are accessed securely by users.
- (b). The user’s details along with the token information will also be stored in the browser cookie through the Web SDK, to ensure their session is maintained.
Workflow of an authenticated user logging into your application while the token is still active
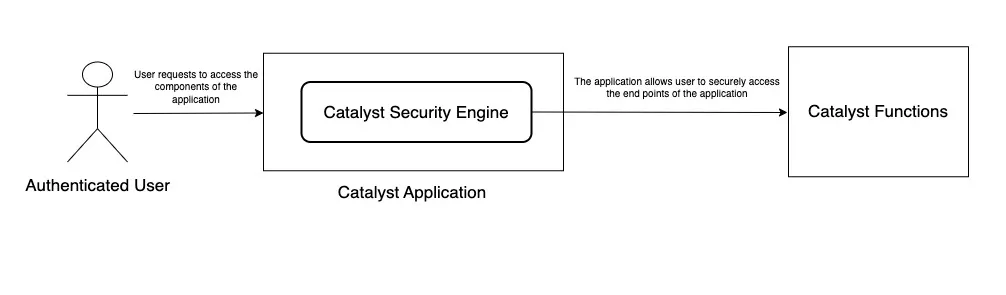
After a user is authenticated and the login session is persisting, the user can securely access all the end points of your application until the time the token is active.
Last Updated 2025-05-26 17:57:12 +0530 +0530
Yes
No
Send your feedback to us